The concept of a Virtual Private Network is relatively new. And, if you’ve never used one, it might seem like this is complicated technology. Well, not really: modern-day VPNs are very intuitive and easy to use. In this post, we’ll tell you how a VPN works, why would a regular user need one, and what it’s all about.
You’ll also find a detailed guide on how to pick a VPN that is right for you. There are many different offers on the market, and sometimes, it can be pretty hard to understand which one is best for your current situation. While most users use VPNs for security and privacy, they can also be used for unblocking geo-restricted content and torrenting. We’ll talk about it all later in this article.
How Does a VPN Work?
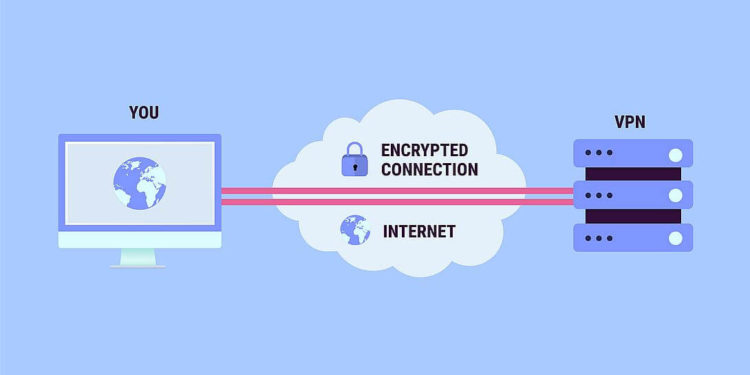
 A VPN re-routes the connection through a secure server and changes the user’s IP, thus turning them into digital shadows. When you switch a VPN on, it immediately starts to encrypt the data before sending it to the ISP (or the Wi-Fi hotspot). Next, the data goes directly to the Virtual Private Network, and only then to your favorite browser. The websites “think” that the data is coming from the VPN server, not your computer/mobile device.
A VPN re-routes the connection through a secure server and changes the user’s IP, thus turning them into digital shadows. When you switch a VPN on, it immediately starts to encrypt the data before sending it to the ISP (or the Wi-Fi hotspot). Next, the data goes directly to the Virtual Private Network, and only then to your favorite browser. The websites “think” that the data is coming from the VPN server, not your computer/mobile device.
That’s how the VPN masks the user’s actual IP and keeps hackers at bay. Without a VPN, there’s no encryption and no routing through a secure server. All of your online activity is out there in the open, vulnerable to potential attacks and surveillance by third parties.
Here’s how the Internet works: every single website is stored on a server, and they continuously communicate with each other. To let a user browse web pages online, they share data regularly. It allows people from different corners of the planet to access websites that are located thousands of miles away.
But, again, this creates considerable flaws in security. If you’re not worried about someone else seeing what you see on the screen of your device, then there’s nothing to worry about.
However, business emails, online banking, and anything else that has to do with sensitive data is a major reason for your concern. With a VPN, your data is first encrypted by the best protocols, then goes to the ISP, and then to one of the service’s servers. To put it simply, a Virtual Private Network connects to the web on your behalf.
VPN Protocols
And now that we’ve learned how a VPN works let us take a quick look at the available protocols. They define how the provider transfers data from your device to the servers. OpenVPN is the most popular protocol, while IKEv2 is the most secure one. SSTP, PPTP, and L2TP are also very popular.

- OpenVPN. Internationally known as the most user-friendly protocol, OpenVPN doesn’t have any significant flaws. It is an open-source project, meaning developers around the globe can access its code and improve it. This protocol is based on SSL/TLS, which makes it easier to work with the source. It encrypts the connection by using unique keys known only to the two ends of an online transmission.
- IKEv2. AKA the Internet Key Exchange 2, this protocol was entirely created by Microsoft. It’s based on the company’s previous developments and is currently the most secure protocol on the market. Sadly, at the moment, it doesn’t offer as much cross-platform compatibility as the other protocols.
- SSTP. This one stands for the Secure Socket Tunneling Protocol. Here, we have another Microsoft-built protocol. It also implements the SSL/TLS encryption – a standard in modern-day online encryption. While SSTP is slightly less secure than IKEv2, it is on par with OpenVPN and is an overall excellent choice for online security.
- PPTP – the Point-To-Point Tunneling Protocol. Again, developed by Microsoft, PPTP is one of the original (and oldest) protocols and has a series of security flaws. It is built into the Windows OS and can work with decades-old computers, which is a big pro. However, it can’t compete with the modern-day protocols, and we strongly advise against using it.
- L2TP/IPSec – the Layer2 Tunneling Protocol. While this is a far better choice compared to PPTP, it’s still not the best pick for privacy and security today. Yes, it does use keys for establishing a protected and encrypted connection, but, since it’s heavily based on PPTP, you won’t be safe with it. The addition of IPSec to the mix does help, but rumors claim NSA can easily break through it.
What Can a VPN Do for You?
The ability to change the user’s IP is the most significant advantage of a VPN, along with traffic encryption. Here’s how that improves security and privacy:
- Every single site you visit thinks that the VPN server, not you generate all of your traffic.
- With a VPN switched on, it is almost impossible to pinpoint your location and to identify your device as the traffic origin. It is equally hard to monitor your online activity.
- And even when someone does manage to monitor your actions online, all they see is encrypted info, not the raw data that could hurt you in any way.
All you have to do to protect yourself from online threats is switch the VPN on – it will do the rest.

Still, those these aren’t the only benefits of using a Virtual Private Network. Geo-restricted content is another concern for modern-day users, and with the help of a decent VPN service, you can easily access blocked content. It all comes down to connecting to a server located in the same country (say, the US for Netflix), and that’s it!
Finally, VPNs are also an excellent tool for trouble-free torrenting. Downloading copyrighted content is illegal, and it’s not rare for the police to come knocking at the door of an avid torrenting fan.
Even if you’re just sharing personal files among your friends, the ISP can easily implement throttling and reduce your Internet speed. With a VPN, the ISP won’t know that you’re using the P2P protocol and you’ll get to enjoy hassle-free torrenting.
Can One Stay Anonymous with a VPN?
The short answer is no, Virtual Private Networks can’t provide 100% anonymity. There are other things in addition to IP address that will let those willing track you down. Your OS, your browser, the applications you use all matter. On the bright side, they are quite impressive in protecting a user’s privacy.
As we already discussed, without a VPN, your connection isn’t protected in any way. That means the owner of the local café’s Wi-Fi, your ISP, or even any server that you connect through can take sneak peeks at your data. Furthermore, a hacker with the right knowledge and set of tools will be able to take control of your device and steal sensitive data.
By using a VPN, you can avoid the majority of these problems. By encrypting the user’s transmission, a VPN service makes the world think that it’s one of its servers visiting all those websites, not the user routing traffic through it.
 This is important: you shouldn’t ever blindly trust a VPN provider. Make sure to learn as much about its privacy policy as you can before committing to it. The thing is – it’s not rare for certain providers to share info with third parties, including world governments. There are some key elements that you should consider.
This is important: you shouldn’t ever blindly trust a VPN provider. Make sure to learn as much about its privacy policy as you can before committing to it. The thing is – it’s not rare for certain providers to share info with third parties, including world governments. There are some key elements that you should consider.
Does the VPN Provider Keep Logs?
You can always find the privacy policy on the official websites. Most of the time, the policies are open and transparent. However, sometimes, third-party testers find out that individual companies don’t follow their own policies. The list of logs may include connection start/end time, bandwidth, payment records, and even personal IP.
Again, make a habit of checking the privacy policy before committing to a VPN. Chances are, they’ll be gathering your data and sharing it with third parties without you even knowing it. This is especially true for free products that “attack” the users with numerous ads.
What About the Jurisdiction?
This depends on where the VPN’s HQ is. For example, ExpressVPN is located in the BVI (British Virgin Islands), while NordVPN’s HQ is in Panama. These two countries aren’t a part of the Five-Eyes/Fourteen-Eyes surveillance alliances.
IPVanish, in turn, is in the US, which means the company has to follow the local online privacy laws. The United States government is known to spy on people without their direct permission. And, IPVanish will have to comply with its requests to share personal data of the users. This is 100% legal; so, the best thing you can do is pick a VPN that is outside of any of the alliances mentioned above.

How to Choose a Reliable VPN?
We just discussed the most critical aspects of a Virtual Private Network. But, that’s not all, and the following list includes more important questions that you should ask before purchasing a plan:
Is security good enough? What encryption protocols do you get access to with a given VPN – are OpenVPN and IKEv2 available? If you can’t use at least one of these protocols, then you should forget about this provider. The AES 256-bit, also known as the military-grade encryption, is the most advanced encryption of our time. Sometimes, VPNs offer a choice between 256 bit (the best protection, but a bit slow), and 128 bit (much faster, but worse security).
Are there any data limits? The best providers like ExpressVPN, CyberGhost, NordVPN, and others, don’t’ have any data limits. That means you have unlimited bandwidth and won’t ever have to worry about it. Most free services and free trials do have data caps, though.
How many servers does the provider have? This is important if you’re a big fan of streaming platforms and want to watch Netflix, BBC iPlayer, and other services. Besides, the more servers at your disposal, the better chance you’ll have at enjoying a stable connection.
How many simultaneous connections does your VPN support? For an average user, three to five connections (devices) are more than enough. With ExpressVPN, you can only protect up to three devices, while IPVanish can easily take up to ten connections under its wing.
How much does it cost? Don’t forget to check the reviews of several services to find the best deals. Discounts and incentives are a regular thing, and the longer your commitment, the lower the monthly price-tag. Beware: as we mentioned earlier, free products usually send tons of ads your way and even sell personal info to third parties.